Attackers are increasingly abusing devices configured to publicly reply to SNMP (Simple Network Management Protocol) requests over the internet to amplify distributed denial-of-service attacks.
This amplification technique, which is additionally known as reflection, can on paper work with any protocol that's vulnerable to science (Internet Protocol) address spoofing and might generate giant responses to significantly smaller queries. Attackers can craft requests that seem to originate from the science address of their intended victim in order to trick servers that accept requests over such protocols from the internet to flood the victim with information.
Many DDoS attacks within the past year have used misconfigured DNS (Domain Name System) and NTP (Network Time Protocol) servers for amplification. However, devices that support SNMP, a protocol designed to allow the observation of network-attached devices by querying info about their configuration, may be abused if the SNMP service is directly exposed to the internet. SNMP-enabled devices with such configurations are often found each in home and business environments and embody printers, switches, firewalls and routers.
Sunday, May 25, 2014
What is DDoS denial of service?
What everyone needs to know about DDos?
DDoS stands for Distributed Denial of Service. A malicious hacker uses a DDoS attack to form a computer resource (i.e. – website, application, e-mail, voicemail, network) stop responding to legitimate users. The malicious hacker will this by commanding a fleet of remotely-controlled computers to send a flood of network traffic to the target. The target becomes therefore busy dealing with the attacker’s requests that it doesn’t have time to reply to legitimate users’ requests. that can cause the target system to prevent responding, resulting in long delays and outages.
What is a distributed attack?
One DDoSer can do a lot of injury. These denial of service attacks area unit known as distributed as a result of they are available from several computers right away. A DDoSer controls an outsized variety of computers that have been infected by a Trojan virus. The virus is a small application that allows remote command-and-control capabilities of the computer while not the user’s information.
What is a zombie and a botnet?
The virus-infected computers area unit known as zombies – as a result of they are doing whatever the DDoSer commands them to try and do. an outsized cluster of zombie computers is termed a robot network, or botnet.
DDoS stands for Distributed Denial of Service. A malicious hacker uses a DDoS attack to form a computer resource (i.e. – website, application, e-mail, voicemail, network) stop responding to legitimate users. The malicious hacker will this by commanding a fleet of remotely-controlled computers to send a flood of network traffic to the target. The target becomes therefore busy dealing with the attacker’s requests that it doesn’t have time to reply to legitimate users’ requests. that can cause the target system to prevent responding, resulting in long delays and outages.
What is a distributed attack?
One DDoSer can do a lot of injury. These denial of service attacks area unit known as distributed as a result of they are available from several computers right away. A DDoSer controls an outsized variety of computers that have been infected by a Trojan virus. The virus is a small application that allows remote command-and-control capabilities of the computer while not the user’s information.
What is a zombie and a botnet?
The virus-infected computers area unit known as zombies – as a result of they are doing whatever the DDoSer commands them to try and do. an outsized cluster of zombie computers is termed a robot network, or botnet.
Saturday, May 24, 2014
Universal Acceptance of All Top-Level Domains : Dos and Don’ts
✘ Don’t check domain validity if you don’t need to. A lot of applications don’t need to constrain the domain field, so unless you have a compelling reason to constrain it, leave it open.
✘ Don’t check the length of a domain to determine validity. You can no longer assume domain endings
will be 2 or 3 characters long. They potentially can be between 1 and 63 characters long.
✔ Do use an IDN library to properly convert domain names if they are received in multiple formats. There are many libraries (a lot of them are free) that are used by major software vendors to implement this functionality. Make sure the library supports the most current (“IDNA2008”) standard, as the older standard introduces compatibility issues.
✘ Don’t use a hard-coded list of domains in your application. If you need to check if a domain exists, the best way to do it is using the DNS protocol. A live DNS query happens quickly and will provide your application with the most up-to-date data available.
✔ If you require a hard-coded list, do make sure it is regularly updated (e.g., daily) using an appropriate methodology. ICANN provides some sample toolkits on how this might be done.
✔ Do ask questions if you are not sure. ICANN is happy to help provide advice to software developers and implementers on what is needed. Contact us at: tld-acceptance@icann.org.
✔ Do report websites or software that has problems accepting newer domains. If you notice a website that has problems, let us know and we’ll try to reach out to the operators to encourage them to follow these guidelines.
Thursday, May 22, 2014
Universal Acceptance of All Top-Level Domains
What’s a TLD?
A top-level domain (TLD) is the suffix at the end of a domain name, such as “.com”, “.uk” and “.nz”. It represents the highest level division of the Domain Name System (DNS) hierarchy.
What’s the problem with acceptance of all TLDs?
The Internet is growing. In the 1980s and 1990s, the format of domain names followed a simple pattern. All domains ended with a small number of common 3 character long endings like “.com” and “.net”, or a two-letter code that represented a country like “.de” and “.uk”.
Times have changed. Since 2001, TLDs comprised of more than 3 characters long (think of “.info” or “.museum”) were introduced, and since 2010, non-Latin strings – known as internationalized domain names (IDNs) – have been added to the root zone. The ICANN Board’s approval of the new gTLD program in 2011 will allow for hundreds of additional TLDs to be added. This means that the variety of domain names will expand even further.
Software vendors, web site developers, and others might limit what they allow as a valid domain name in their applications. This might constrain the Internet’s growth, consumer choice and promotion of market competition on-line. The effort toward universal acceptance of domains seeks to ensure that the systems that perform domain name validation do it in a correct way that allows for all valid domains to function correctly. Domains should work regardless of the script they are written in or the time they were implemented: 20 years ago or yesterday.
To properly support today’s DNS, implementers need to deploy software and solutions that cater to all of these developments. Software needs to fully accept all the variety of domain names. This includes domain endings containing 4 or more characters and internationalized domain names.
A top-level domain (TLD) is the suffix at the end of a domain name, such as “.com”, “.uk” and “.nz”. It represents the highest level division of the Domain Name System (DNS) hierarchy.
What’s the problem with acceptance of all TLDs?
The Internet is growing. In the 1980s and 1990s, the format of domain names followed a simple pattern. All domains ended with a small number of common 3 character long endings like “.com” and “.net”, or a two-letter code that represented a country like “.de” and “.uk”.
Times have changed. Since 2001, TLDs comprised of more than 3 characters long (think of “.info” or “.museum”) were introduced, and since 2010, non-Latin strings – known as internationalized domain names (IDNs) – have been added to the root zone. The ICANN Board’s approval of the new gTLD program in 2011 will allow for hundreds of additional TLDs to be added. This means that the variety of domain names will expand even further.
Software vendors, web site developers, and others might limit what they allow as a valid domain name in their applications. This might constrain the Internet’s growth, consumer choice and promotion of market competition on-line. The effort toward universal acceptance of domains seeks to ensure that the systems that perform domain name validation do it in a correct way that allows for all valid domains to function correctly. Domains should work regardless of the script they are written in or the time they were implemented: 20 years ago or yesterday.
To properly support today’s DNS, implementers need to deploy software and solutions that cater to all of these developments. Software needs to fully accept all the variety of domain names. This includes domain endings containing 4 or more characters and internationalized domain names.
Tuesday, May 20, 2014
The Benefits of Acunetix WVS AcuSensor
Acunetix AcuSensor Technology is a new security technology that allows you to identify more vulnerabilities than a traditional Web Application Scanner, whilst generating less false positives. In addition it indicates exactly where in your code the vulnerability is and reports also debug information.
The increased accuracy is achieved by combining black box scanning techniques with feedback from sensors placed inside the source code while the source code is executed. Black box scanning does not know how the application reacts and source code analyzers do not understand how the application will behave while it is being attacked. Therefore combining these techniques together achieves more relevant results than using source code analyzers and black box scanning independently.
AcuSensor Technology does not require .NET source code; it can be injected in already compiled .NET applications! Thus there is no need to install a compiler or obtain the web applications’ source code, which is a big advantage when using a third party .NET application. In case of PHP web applications, the source is already available.
To date, Acunetix is the leading and only Web Vulnerability Scanner to implement this technology.
Advantages of Using Acunetix AcuSensor Technology
- Allows you to locate and fix the vulnerability faster because of the ability to provide more information about the vulnerability, such as source code line number, stack trace, affected SQL query.
- We can significantly reduce false positives when scanning a website because we can internally understand the behavior of the web application better.
- Can alert you of web application configuration problems which could result in a vulnerable application or expose internal application details. E.g. If ‘custom errors’ are enabled in .NET, this could expose sensitive application details to a malicious user.
- Detect many more SQL injection vulnerabilities. Previously SQL injection vulnerabilities could only be found if database errors were reported or via other common techniques.
- Ability to detect SQL Injection vulnerabilities in all SQL statements, including in SQL INSERT statements. With a black box scanner such SQL injections vulnerabilities cannot be found.
- Ability to know about all the files present and accessible though the web server. If an attacker gains access to the website and create a backdoor file in the application directory, the file will be found and scanned when using the AcuSensor Technology and you will be alerted.
- AcuSensor Technology is able to intercept all web application inputs and builds a comprehensive list with all possible inputs in the website and tests them.
- No need to write URL rewrite rules when scanning web applications which use search engine friendly URL’s! Using AcuSensor Technology the scanner is able to rewrite SEO URL’s on the fly.
- Ability to test for arbitrary file creating and deletion vulnerabilities. E.g. Through a vulnerable script a malicious user can create a file in the web application directory and execute it to have privileged access, or delete sensitive web application files.
- Ability to test for email injection. E.g. A malicious user may append additional information such as a list of recipients or additional information to the message body to a vulnerable web form, to spam a large number of recipients anonymously.
How it Works
When AcuSensor Technology is used, it communicates with the web server to find out about the web application configuration and the web application platform (such as PHP and .NET) configuration. Once triggered from the Acunetix WVS scanner, the sensor gets a listing of all the files present in the web application directory, even of those which are not linked to through the website. It also gathers a list of all the web application inputs. Since it knows what kind of inputs the application expects, it can launch a broader range of tests against the application.
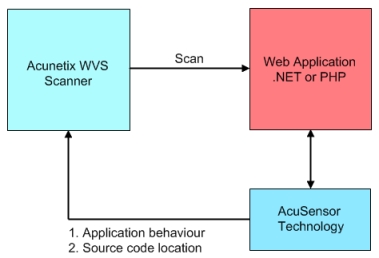
Screenshot 1 - AcuSensor Technology Functionality Diagram
It has also the ability to scan all SQL transactions taking place between the web application and the database when the web application is being scanned. It hooks between the web application and the database and is able to trace SQL injection vulnerabilities in the code without relying on database errors like other typical scanners do.
AcuSensor Technology Vulnerability Reporting
Unlike other vulnerabilities found by typical scans, a vulnerability reported from the AcuSensor Technology contains much more detailed information. As seen in the examples below, it can contain details such as source code line number, stack trace, affected SQL query etc. Each vulnerability found by AcuSensor Technology, will be marked with ‘(AS)’ in the title.
Example 1: SQL Injection Reported by Acunetix AcuSensor Technology
For the reported SQL injection featured in the screenshot below, the SQL query including the injected content which results into an SQL injection vulnerability is shown. The stack trace information is also displayed, to guide the developer where exactly the problem is.
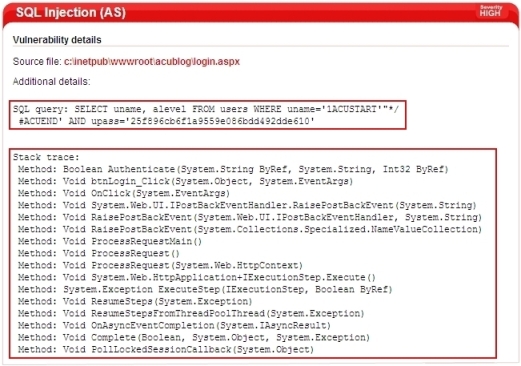
Screenshot 2 - SQL Injection Reported by AcuSensor Technology
Example 2: Code Injection Reported by Acunetix AcuSensor Technology
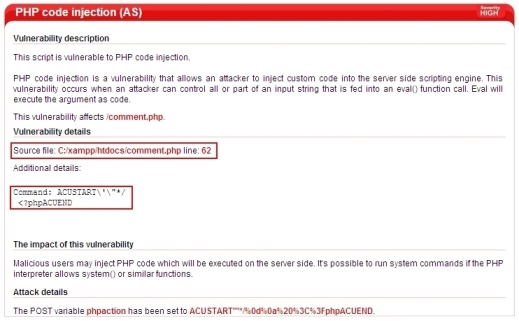
For the reported PHP code injection featured in the screenshot below, the vulnerable file name is displayed including the line number of the code which leads to the reported vulnerability. The injected code is also displayed under ‘Attack details’.
Screenshot 3 - PHP Code Injection Reported by AcuSensor Technology
Conclusion
As seen above, using the AcuSensor Technology has many advantages. Apart from the above mentioned advantages, information provided by the AcuSensor Technology helps the developer trace vulnerabilities and fix them in a much shorter time. It also helps them understand what was wrong in the code to allow such vulnerabilities to happen. From this, developers proactively learn more about vulnerabilities and it helps them in writing more secure code for future web applications and increases web security awareness.
Source : Acunetix
ICANN : Final Initial Evaluation Results Published
 The Internet Corporation for Assigned Names and Numbers (ICANN) has finished the Initial Evaaluation for the 1930 new gTLD applications.
The Internet Corporation for Assigned Names and Numbers (ICANN) has finished the Initial Evaaluation for the 1930 new gTLD applications.
Out of the 1930 new gTLD applications, only 1783 passed the Initial Evaluation (IE).Some of the applications have been withdrawn without even reaching the Initial Evaluation.
ICANN had three possible outcomes of Initial Evaluation :
-Pass
-Eligible for Extended Evaluation
-Ineligible for Further Review
33 out of the initial 1930 new gTLD applications have passed the Extended Evaluation. Extended Evaluation is available for those that did not probide sufficient information in Initial Evaluation to pass technical, financial, registry services or geographic names review.
You can see the status of all new gTLDs here.
Source: Domainnews
Monday, May 19, 2014
ICANN Orders Bulk Transfer
ICANN Orders Bulk Transfer of Domain Names from De-Accredited Registrars
The Internet Corporation for Assigned Names and Numbers (ICANN) has authorized the bulk transfer of generic top-level domains (gTLDs) from two registrars after compliance actions resulted in their de-accrediation. In news alerts issued the 5th and 10th of March, ICANN announced that the Registrar Accreditation Agreements with domain registrars Asadal, Inc. and ABSYSTEMS INC (d/b/a YourNameMonkey.com), respectively, had recently terminated.
Following its De-Accreditated Registrar Transition Procedure, ICANN identified a gaining registrar for the gTLD names formerly managed by the de-accreditated registrars. ICANN authorized bulk transfers of the affected names according to the Inter-Registrar Transfer Policy (IRTP) in order to protect domain owners from their registrar’s loss of accreditation. Domain owners with names registered with Asadal, Inc. are being informed of their domain’s transfer to the gaining registrar Gabia, Inc., and those with names at YourNameMonkey.com are being informed of their domain’s transfer to EnCirca, Inc.
Former customers of the de-accredited registrars should receive a notice of the transfer from the new gaining side registrar with instructions for continued management of their domains. Those affected by the bulk transfer who do not receive noticed from their new registrar should contact Gabia at http://www.internic.net/registrars/registrar-244.html, or EnCirca at http://www.internic.net/registrars/registrar-455.html.
Registrants preferring to move their domain to a registrar besides the one chosen by ICANN may do so, provided that EnCirca and Gabia may deny transfers for the first 60 days following the bulk transfer in accordance with the IRTP. There is no cost to registrants for the bulk transfer but unlike a normal inter-registrar transfer, there will not be an extension of the registration for an additional year. If your domains are scheduled to expire soon its important you contact the gaining side registrar immediately to prevent the loss of your domain.
Source:Sedo
Sunday, May 18, 2014
Registration Process for .EDU.IN and .AC.IN Domain Name
Domain Registration Process
Whois for the desired
domain name
Review the Domain
naming conventions/Guidelines and ensure that the desired domain name complies with the
conventions
|
THE REGISTRANT'S
REPRESENTATIONS
|
||||||||||||||||||
|
By applying to
register a domain name, or by asking Registrar to maintain or renew a domain
name registration, the Registrant represents and warrants to the Registrar
that:
|
||||||||||||||||||
|
||||||||||||||||||
|
It is the
Registrant's responsibility to determine whether the Registrant's domain name
registration infringes or violates someone else's rights.
|
Thursday, May 15, 2014
Choosing the correct Dedicated Server
Choosing the correct
Dedicated Server Makes Business Sense
“Someone can always do your job a little
better or faster or cheaper than you can.”- Seth Godin
The selling guru’s statement echoes the emotions of this
trends in business. Most webmasters feel growing pains after they ought to
expand from their existing setup to a bigger one. But, the pinch or the impact
actually strikes when a rival offers the same service with better deals and
quicker speed on-line. Your rival has most likely captive onto an avid server.
A Dedicated Server Brings
your Business Up to speed
Dedicated server hosting usually involves one pc that is
dedicated towards the needs of a specific network. By having a server that's
dedicated towards hosting, storing information or perhaps communication with
other computers, businesses have the advantage of area, time and future
resources. Here’s a look at the advantages of getting an avid server.
Dedicated or shared?
Managed dedicated server hosting is practically viable
despite being slightly dearer than shared server hosting. when it comes to the
decision-making process for a shared server or an avid server, check for
factors which will make it easier for your business to propel ahead. we give a
elaborate run-down of the distinction between dedicated and shared servers.
Choosing the one:
Choosing between an avid server and a shared one ought to be
practically easy. In a trial to decide on convenience and low cost, most
businesses opt to escort shared servers. Yet, despite the cost facet, there area
unit some definite benefits of getting dedicated servers. So, if you are aiming
to choose an avid server instead of a shared server, then, look out for these
factors to improve your higher cognitive process. Here’s what ought to inspect
in your server:
- · Check the compatibility of the OS in your server. Also, the open source stack involves ought to be vetted out for Ruby on Rails, Linux or perhaps an Apache/php/mysql server.
- · By preferring the technology stack, you'll assess the quantity of RAM that you simply want for your design.
- · To traumatize performance problems, its best that you simply choose an avid server like those offered by recognized server suppliers just like the ones at the icloudJunction.
- · In order to host pictures, videos or any other transmission options like flash applications, its best to decide on a server that offers the optimal information measure and disc space.
- · Check for monthly costs and setup costs. Compare the rates for software licensing, upgrades and components, with the exception of other management plans and extra services.
Featuring amongst the top of the lists of the most effective
suppliers of dedicated servers is the icloudJunction. Compared to relatively
sensible suppliers like Godaddy.com, icloudJunction is additional well-liked for
the subsequent three reasons:
Flexibility:
icloudJunction dedicated servers area unit designed to suit the needs of these
involved in web hosting for personal use or for any business.
Fair prices: If
you thought that dedicated server web hosting is pricey business, move removed
from the other suppliers and inspect the latest offerings from icloudJunction.
Reliable and bankable
support: when it comes to the near zero period of time and around the clock
support, then it’s time that you simply enter the support staff at the
icloudJunction.
“As the statistics show, sixty two of all websites in Alexa prime 10k
by traffic area unit hosted on Dedicated Servers."
Lastly, the selection of the best server is it dedicated or
shared ought to be determined solely the conditions people who area unit unique
to your business or personal use. Don’t hesitate to explore for the best
distributor of servers that follow the conditions based on your requirements.
Thursday, May 1, 2014
Secure your LAMP based VPS and Dedicated Web Servers
The Internet has given United States the ability to shop for product, create payments etc instantly from the comfort of our own homes. but beside these advantages, there's Associate in Nursing underlying cyber security threat at hand. it had been recently unconcealed that quite 360 million stolen Credit Cards accounts were up purchasable on the cyber black market. With many similar incidents like this returning to the fore within the past, it's essential to make sure that you simply keep crucial info regarding your customers’ secure and save yourself many bucks in shopper lawsuits.
We’ve place along slightly guide to assist you scale back the chance of your your LAMP based mostly servers from obtaining hacked. LAMP is one in all the foremost popularly used Application Stacks. It stands for UNIX system, Apache, PHP and MySQL.
Mitigate the risks of your servers being attacked
The Apache net Server is one in all the foremost normally used net Servers. but like most different software package, it needs acceptable settings, observance and maintenance to protect against vulnerabilities. during this post, we are going to cowl each General pointers that you simply will follow to secure your server, additionally as bound specific steps that you simply ought to address to mitigate the injury caused by such attacks.
General Security pointers to be followed for securing your net Server
- Sign up for updates and announcements from the net Server listing.
- Upgrade to the newest version whenever there's Associate in Nursing update.
- Install solely the modules you need and disable excess ones.
- Make sure you log all admin level accesses with date, times and usernames
- Do not show your server version or OS version in error messages.
For Servers with Apache:
1. Hide the Apache Version variety, and different sensitive info
It is essential to cover the Apache Version variety your server is running, additionally as different sensitive info. you'll try this by following the straightforward steps listed below.
Add or Edit the subsequent 2 directives in your httpd.conf file
ServerSignature Off
ServerTokens Prod
The ServerSignature seems on the lowest of pages generated by apache like 404 pages, directory listings, etc.
The ServerTokens directive is employed to see what Apache can place within the Server hypertext transfer protocol response header. By setting it to Prod it sets the hypertext transfer protocol response header as follows:
Server: Apache
2. certify apache is running underneath its own user account and cluster
When Apache is put in, the default user is ready as “nobody”. but if there different applications that additionally run because the user no one on your system, then a compromise of apache can even compromise different installations. it's best to feature a separate user “apache” and so modify the subsequent directives in httpd.conf to run apache because it own user.
User apache
Group apache
3. make sure that files outside the net root directory aren't accessed.
It is continually smart apply to limit access for files outside the net root directory to take care of security and make sure that these files square measure solely accessed by folks that have to be compelled to access them.
<Directory />
Order Deny,Allow
Deny from all
Options None
AllowOverride None
</Directory>
<Directory /html>
Order Allow,Deny
Allow from all
</Directory>
Order Deny,Allow
Deny from all
Options None
AllowOverride None
</Directory>
<Directory /html>
Order Allow,Deny
Allow from all
</Directory>
Note that as a result of we tend to set “Options None” and “AllowOverride None “this can shut down all choices and overrides for the server. You currently got to add them expressly for every directory that needs Associate in Nursing choice or Override.
4. shut down directory browsing, Follow symbolic links and CGI execution
You can try this with Associate in Nursing choices directive within a Directory tag.
If you would like to show off all choices merely use:
Options None
If you simply need to show off some, separate every choice with an area in your choices directive:
Options -ExecCGI -FollowSymLinks -Indexes
5. Install modsecurity
ModSecurity is Associate in Nursing Apache add on module which might sight and stop hypertext transfer protocol attacks. It will are available in extremely handy in preventing SQL injections just in case your developers forget to feature input validation or determine and block info revealing problems like unseaworthy elaborate error messages, social insurance Numbers or mastercard Numbers. Follow these steps to put in mod-security
On CentOS:
yum install mod_security
On Ubuntu:
apt-get install mod_security.
service httpd restart
6. Disable any excess modules
There square measure many modules that square measure enabled on your Apache net Server that you simply might not want. to look for modules put in run:
grep LoadModule httpd.conf
Here square measure some modules that square measure generally enabled however usually not needed:
mod_imap
mod_include
mod_info
mod_userdir
mod_status
mod_cgi
mod_autoindex.
To disable them add a # check in front of them.
You can additionally bear the Apache module documentation and disable or alter any that you simply want.
7. Lower the Timeout worth
The default Timeout directive is ready to three hundred seconds. Decreasing this worth help’s mitigating the potential effects of a denial of service attack.
Timeout 45
8. Limit massive requests
In order to mitigate the consequences of a denial of service attack, limit the number of body that may be sent in Associate in Nursing hypertext transfer protocol request. If you are doing not have massive uploads then you'll limit this to 1Mb via the below directive.
LimitRequestBody 1048576
Application and Database Security
SQL injection is another common method of extracting knowledge from poorly coded websites. Here is however you'll forestall it and different such attacks.
- Ensure your Applications like Joomla, WordPress, Drupal etc square measure upto date.
- Subscribe to Bug updates and Vulnerability reports.
- Try and avoid world writable 777 permissions your files or folders.
- Regularly check for viruses or infections by scanning your net package.
- If you're victimization MySQL or MariaDB run the mysql secure installation script.
- If your application needs you to store wind like username, passwords, mastercard knowledge etc. then make sure that all communication is encrypted by employing a Digital Certificate.
For servers with PHP:
1. Run PHP as a separate User
It is suggested to put in php as a separate user than as Associate in Nursing Apache Module. If you put in php as Associate in Nursing Apache Module then php can run with the apache user permission and any compromise of a vulnerable php script will cause a server wide compromise.
A better way to install php would be with php-fpm a fastcgi method manager that permits you to run and manage php scripts as a separate user.
2. Use the POST methodology to pass vital parameters like credit card info
Many developers already recognize this. PHP has 2 ways to pass variable info via a type the GET methodology and also the POST methodology. the foremost vital distinction between these ways is that the GET methodology makes your pass info visible to everybody via a URL whereas POST methodology doesn't. thence sensitive info like usernames, passwords must always be passed via the POST methodology.
3. continually Validate type and Text Input
Cross web site scripting and SQL injection will each be prevented if type or file input is valid.
Cross web site scripting permits a hacker to run malicious code on your server by merely uploading a file with malicious code in it to be run on the server and SQL injection permits a hacker to urge access to your info by injecting malicious queries in your type to urge info info like table name. an easy thanks to validate php code is found at
4 . Hide the PHP version
Open php.ini and add the subsequent
Vim /etc/php.ini
expose_php = Off
5.Log all php errors to a file and not on the web site
display_errors = Off
log_errors = On
error_log = /var/log/httpd/php_error.log
For servers with MySQL or MariaDB:
1. Run MySQL Secure Install
After putting in MySQL run the mysql_secure_installation script.
sudo /usr/bin/mysql_secure_installation
This script can prompt you to feature a mysql root secret, lock root access to localhost and take away any unwanted infos just like the take a look at database.
2. Secure MySQL users and database
Log into your MySQL Server and make sure that all MySQL users have a secret and delete any unwanted user. Grant access to solely those databases that the individual users would use.
Following the steps elaborate on top of, you'll go an extended method in making certain that your customer’s knowledge remains secure. within the next article i'll add detail steps on UNIX system OS and Firewall Security.
Let us recognize if these techniques were useful by effort a comment below
Subscribe to:
Posts (Atom)